Data Leakage: What Are They?
It’s common knowledge that people and companies are losing data to hackers. We’ve seen it through data leaks in companies like Facebook to increase identity theft. Many people accept that their data will be a part of a leak at least once in their life. Common cyber attacks target specific individuals to gain access to information that can be used for personal gain. Additionally, hackers target particular individuals through various ploys to gain information. Finally, hackers can access your organization’s systems through multiple methods and wreak havoc. However, to recognize how to protect yourself from these attacks, you must be able to identify these attacks and learn how to prevent them.
Phishing
Phishing is the practice of using fake emails, calls, or texts to mass audiences in the hope of receiving individuals’ private information. Hackers often do this using a unique link or attachment. Once opened, the link downloads a virus to the device. This gives them access to the individuals’ network and personal data, like passwords or credit card information. Hackers commonly use spear-phishing, targeting specific individuals to gain detailed data or information. The hacker will research information about the individual utilizing public records to tailor their emails to appeal to the individual. They will then use emails for their attack system to create a data leakage as it is a fast and easy way to gain information from a business.
Business Email Compromises (BEC)
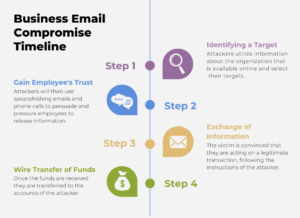
Business Email Compromises, or BEC, are a form of monetary hacking that has become fairly common in businesses over the last few years. This hacking process varies from phishing as its primary goal is to receive money instead of company information. Hackers do this by following a four-step plan:
- Identifying a Target
- Gain Employee’s Trust
- Exchange of Information
- Wire Transfer of Funds
There are two forms of BEC seen today. The first form of BEC uses a company’s vendors’ information. Hackers will change the billing location from the correct address to theirs. Hackers do this by spoofing their emails to mimic a known vendor to change the billing addresses. Many employees fall for this scam as they recognize the vendor but don’t take securing steps. The second type of BEC often occurs with new or unaware employees like assistants and interns. They receive an email from the CEO or upper-level manager asking them to buy gift cards for the business. Then another message asks to transfer the payment information to them over email, text, or mail instead of in person. Utilizing the power dynamic between the two parties, hackers can influence these employees into falling into their trap.
Insider Threats
Insider threats are the risk that employees will use their rank to create data leakage and spread access or information that will harm the organization. These threats can be intentional or unintentional. For example:
- Intentional Threats
- Espionage Actors– Individuals hired by an outsider or competitor to hurt the organization from the inside by obtaining intellectual property.
- Disgruntled Employees– Individuals dissatisfied with the company’s operations and can be motivated by financial gains from outside employers.
- Unintentional Threats
- Compromised or Negligent Employees–Individuals who ignore the secure data handling guidelines and the failure to secure workstations. This mishandling can lead to sharing private information with their personal devices.
In a study done by IBM, 60% of all data breaches are performed by an insider of an organization. Thus, being aware that there is a constant risk for breaches internally can help organizations increase their security training. In addition, businesses can take steps to combat insider threats. This can be done by providing a work environment that fosters a healthy and flexible workplace. This can be done by addressing disgruntled employees’ concerns and vetting new employees. Also, employees being offered the proper training to ensure the workspace is secure can help reduce this risk.
Causes and Concerns of Negligent Employees
Stress
Stress is natural in the workforce. Whether it be caused by multiple due dates or a heavy workload, everyone experiences stress. How people deal with it varies depending on the person, the situation, and other factors. Not addressing the problems within the workplace can adversely affect the individual and their work. This can lead to burnout, failure of basic security policies, and possible data leakage. When working with sensitive information, employees can create gaps in the systems that hackers can identify and easily target. Many employees have noted that when under stress, they break security policies more often than when not. When researching the effects of increased hardship, studies found that 67% of employees broke security policies at least once. This translates to around 1 per 20 tasks performed.
Many employees report that their lack of following security policies comes from three main reasons: the need to accomplish tasks for their job, get something they need, or help others with their work. (Harvard Business Review) Over 18% of offenses done in a company were done by the motivation to assist another co-worker. (Harvard Business Review) However, many employees fail to recognize they can create security breaches themselves.
Covid-19/Work from Home Workers
Since the pandemic started, companies have shifted their work operations to a remote or hybrid setting. We still see over 26% of global companies working remote and 4.7 million people working hybrid work weeks. This shift in the workplace environment has changed how companies operate. For example, many remote workers have noted that their team’s communication has become more informal and less accessible.
Relying on online communication can become more common but has decreased the actual connection between employees. Reduced contact has increased the risk of data leakage by 85% since the pandemic started in 2019 by careless employees. Without the structure of an in-person work environment, employees may not protect their workspaces properly and cause unintentional data leakage.
Lack of Training
One of the main reasons that negligent employees exist is that they are unaware of how their actions lead to a data breach. These actions could result from stress or the new work-from-home system. However, many employees fail to recognize how their efforts can put their company at risk.
Although most organizations conduct security training during their onboarding process, many employees fail to apply these concepts to everyday tasks. Organizations must communicate the importance of employees using these pieces of training in their daily workspaces to reduce the risk of breaches. Repeating these security training yearly as well as after attempts of data violations can prevent data leaks from careless employees. Proper training reduces the risk of data leakage and breaches and saves the company’s security.

About Level365: Level365 offers a complete UCaaS solution with an enterprise voice that is customizable and scalable for your business. Our service seamlessly integrates communication among your desk phones, computers, and mobile devices. This cross-device service helps support remote teams and provides flexibility for onsite staff. The UC platform extends beyond voice communications with Unified Messaging, Presence, Chat/SMS, Cloud Faxing, CRM Integrations, etc.





